The ten most important features / terms of Microsoft Defender for Cloud on Azure
In this article I would like to share with you my favorite ten most important terms of the Microsoft Defender for Cloud service. On Microsoft Defender, there are multiple overviews of security issues and navigating can be daunting, so to make the introduction easier to grasp, I use the following screenshot to mark the features on the UI and then explain each one of them in maximum of three sentences. Lets start.
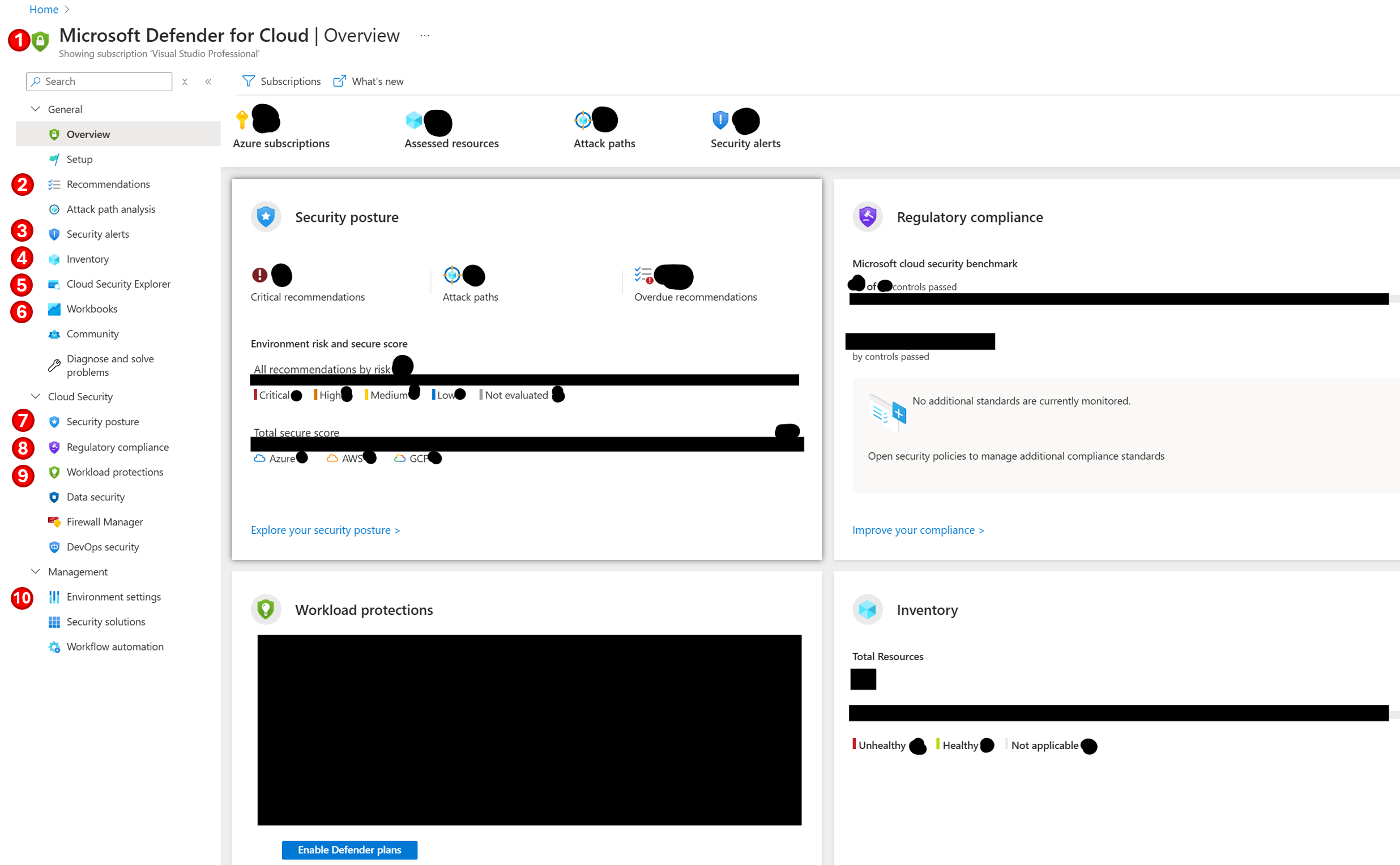
1. The Foundational CSPM and Defender CSPM modes
The Foundational Cloud Security Posture Management (CSPM) is the default mode and is free. Just select the Microsoft Defender for Cloud resource, import one of your subscriptions, give the service some days to gather security information and start fixing issues. In addition, you can pay for the Defender CSPM, which provides extra functionality, such as Attack path analysis or Permissions Management Capability.
2. Recommendations
A list of all security recommendations for your resources proactively assessed from Azure to help you identify and remediate vulnerabilities. Each recommendation contains a title, a more detailed description about the security issue and Governance rules which consist of the person or the team who is going to be responsible for the solution and set the due date. You can either manually resolve the issue with the help of a list of steps or you can also use a Workflow automation where you define a Logic App or an Azure Function triggered every time a new recommendation of a specific type is generated.
3. Security alerts
A list of thrown security alerts for affected resources which is ordered by severity, High, Medium or Low. My favorite row there is the MITRE ATT&CK, which is a set of tactics, techniques, and procedures that are easier to understand. Like in the Recommendations you can either take manual action or trigger an automated response via a Logic App.
4. Inventory
A list of all resources in your subscription and their vulnerabilities. This is my personal favorite overview since I can focus on one resource and solve its security issues.
5. Cloud Security Explorer
A query builder for creating queries and obtaining detailed information about security issues. If you do not want to build a query from scratch, you can use one of the many existing templates.
6. Workbooks
A workbook is a dashboards for gathering and visualizing logged information. The gathered data are exported to the Log Analytics workspace (LAW). Create a new Workbook or use one of the templates, give the data at least one week to be gathered and then start researching. My favorite Workbook is the template for Cost estimation which presents consolidated price estimation for Microsoft Defender for Cloud.
7. Security posture
A list of your Azure subscriptions with a Secure score and the number of Unhealthy resources for each one. You can click on a specific environment and jump to the Recommendations (2).
8. Regulatory compliance
A visualization of the recommendations for your resources ordered by best practices, benchmarks and standards, for example the Microsoft Cloud security benchmark. You can then activate extra compliance rules for your resources. The compliance rules are updated from Microsoft to reflect the latest standards.
9. Workload protections
A visualization of security alerts presented by resource categories, for example Containers, Servers, Storage or App Services. Each resource category is monitored based on default or custom rules.
10. Environment Settings
A list of the registered environments, select one and then on Security policies you can change the CSPM (1) plan, add additional standards or activate Workload protection (9). Additionally you can activate Email notifications, define where logged data are exported either to Log analytics workspace or Event Hub, and when either Streaming updates or Snapshots. Finally, in the settings you can manage the enabled Workflow automation we saw on the Recommendations (2).
Conclusion
Microsoft Defender for Cloud provides a comprehensive set of tools and features to secure your Azure resources effectively. The free features offer a solid starting point for identifying and resolving vulnerabilities, while the paid features, such as Attack path analysis and Permissions Management Capability, add significant value by providing deeper insights and enhanced control over your security environment.