Secure your Azure Functions while in development
Azure Functions are compact and lightweight chunks of code hosted in Azure cloud and can be accessed via HTTP. Since these functions might access sensible data of your application, you want a safe way to call them.
When you are in the development phase, you can use the Host Keys which is a way of authenticating yourself when calling an Azure Function.
When in production, you will have to change to App Service Authentication, since the Host Keys should not be stored in the client’s machines.
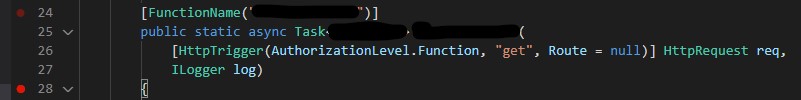
First you will have to define AuthorizationLevel.Function in each of your functions. For example in the following Function we have an HTTP-Trigger:
You will then have to go to the Azure Portal, navigate to the Function App you are working with and select the App Keys option:
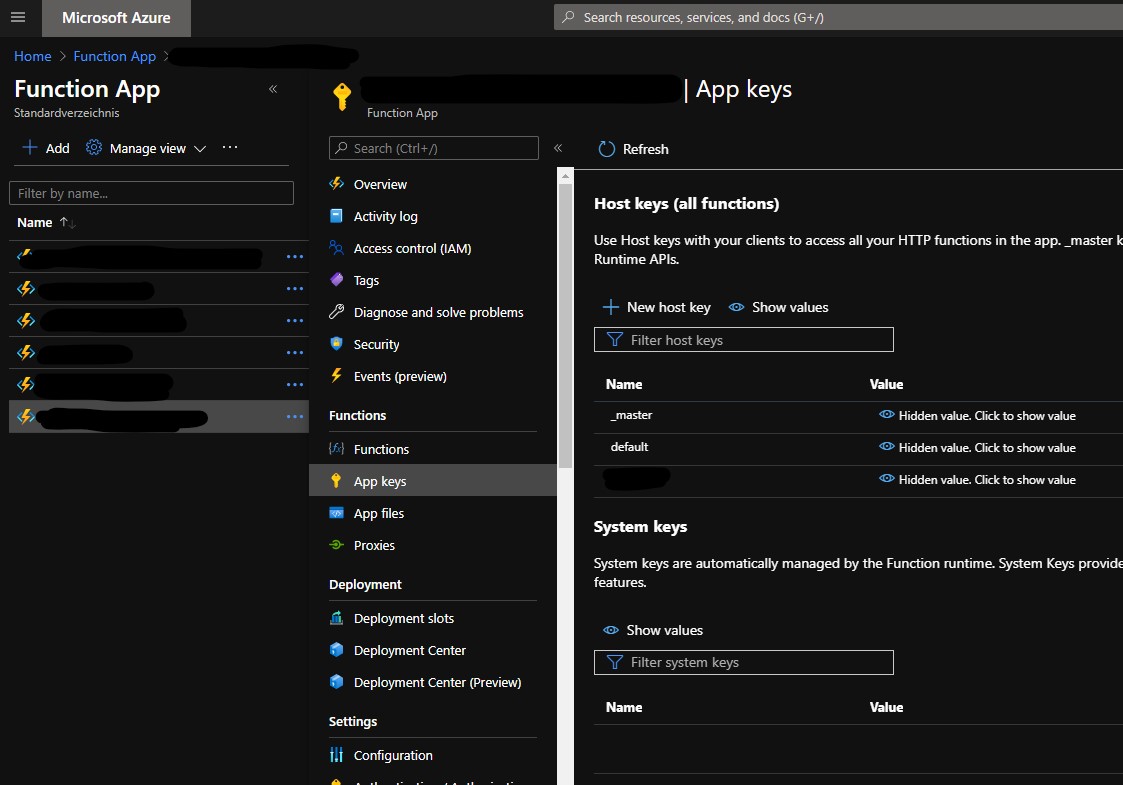
You have now can select between three different types of keys:
- The _master key gives full access to the caller over all Functions of the current Function App. The Admin-mode type
- You can define a new Host key, which gives access either to all Functions or to specific. We are going to use this type of key
- Define a System key
Host key
We first create a new host key and we named it the way we want. We then copy its hidden value and we can use this value in our calls while developing our application:
- Either via Postman, with the x-functions-key Header:
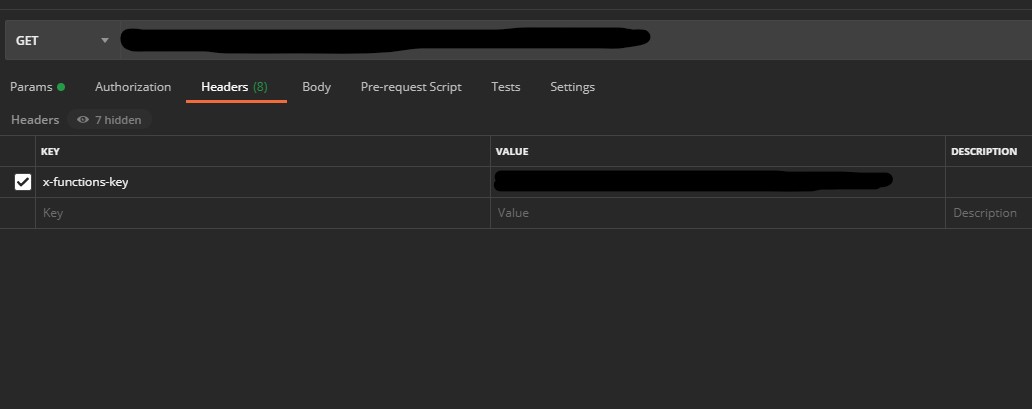
- Or again via Postman with the
?code=APP_KEY_HEREaddition at the URL. You can get the Function URL in Azure Portal:
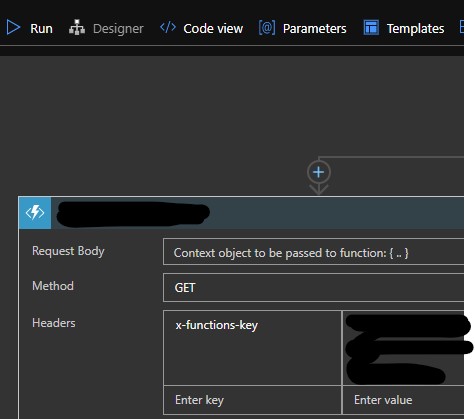
- Or when you are using a Logic App, simple define a new HTTP-Header and paste the App Key into the value field:
Function key
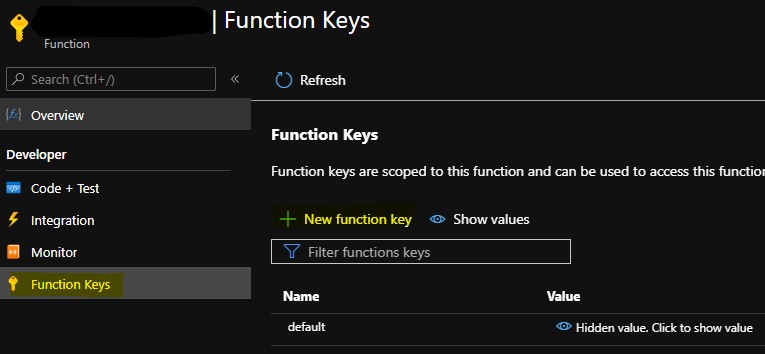
Analog to the Host key, you can use the Function key the same way, however with it you get more granularity since you can authenticate requests on Function level. You can create a new Function key by navigating into the Function you want to secure and then click on Function Keys:
To conclude, I want to mention again that the use of Host keys is advised ONLY while your Functions are in development. When in production, it is more secure to use another way of authentication.