Fixing the "Cannot connect to backend server" error in Azure Application Gateway health checks
When an Application Gateway reports backend health check failures, a frequent but easy-to-miss cause is a TLS negotiation mismatch between the gateway and the backend. This article shows how to diagnose the problem, align TLS settings and probes, validate the fix, and codify the correct configuration in IaC.
Identifying the Issue
- In the Azure Portal, navigate to your Application Gateway (you can find it under
Load balancingservices) - Go to
Monitoringand click onBackend health -
Look for any unhealthy backend pools with the error message:
Cannot connect to backend server. Check whether any NSG/UDR/Firewall is blocking access to the server. Check if application is running on correct port.
Common Root Cause: TLS Version Mismatch
While the error message suggests checking NSG rules and ports, a common cause is a TLS version mismatch between your Application Gateway and the backend service, which in our case is an Azure Function.
Step-by-Step Resolution
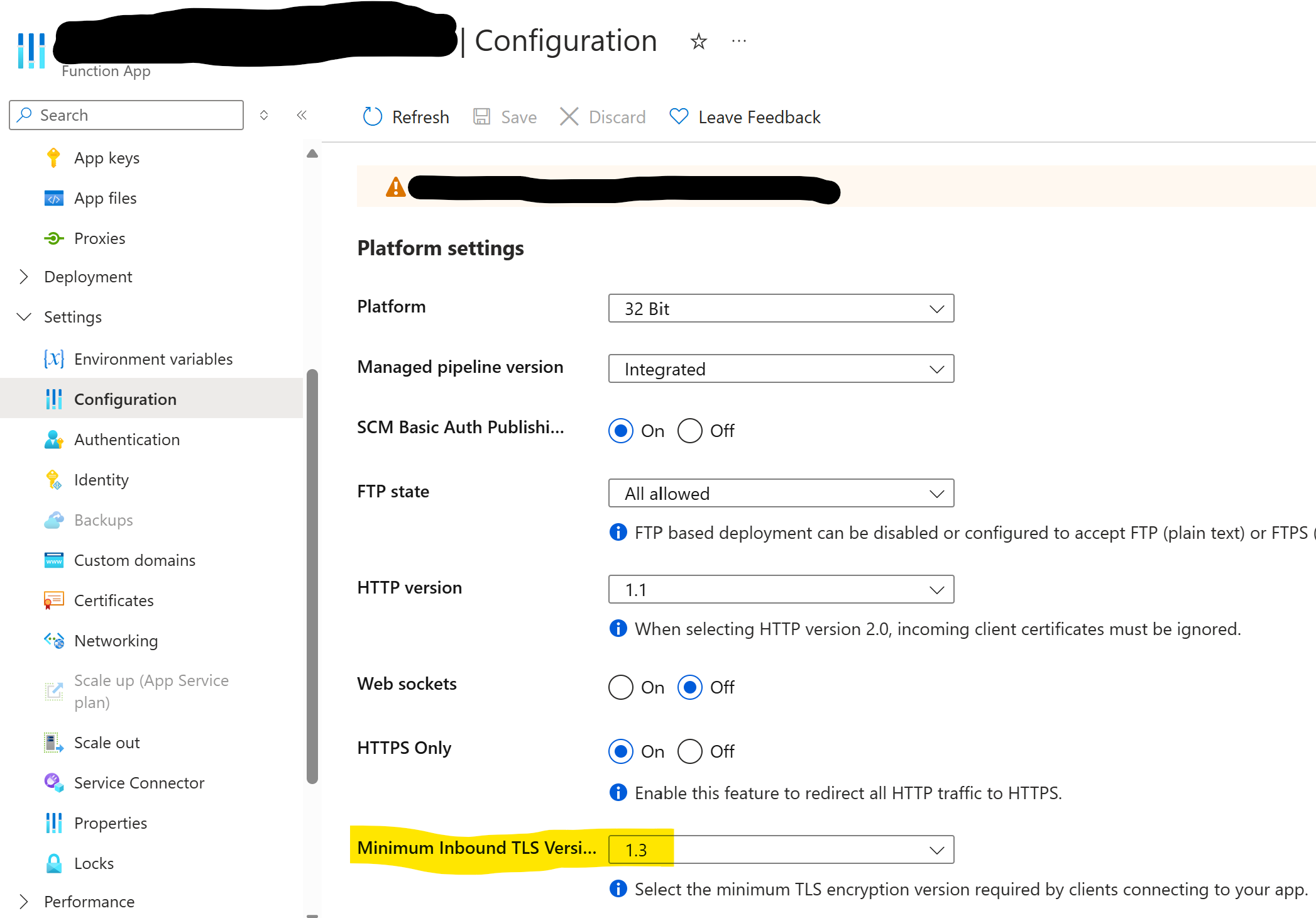
1. Check the backend’s minimum TLS
For an Azure Function:
- Navigate to your Function App
- Go to
Settings→Configuration - Look for
Minimum Inbound TLS Version - If it’s TLS 1.3, the backend will reject TLS 1.0/1.1/1.2
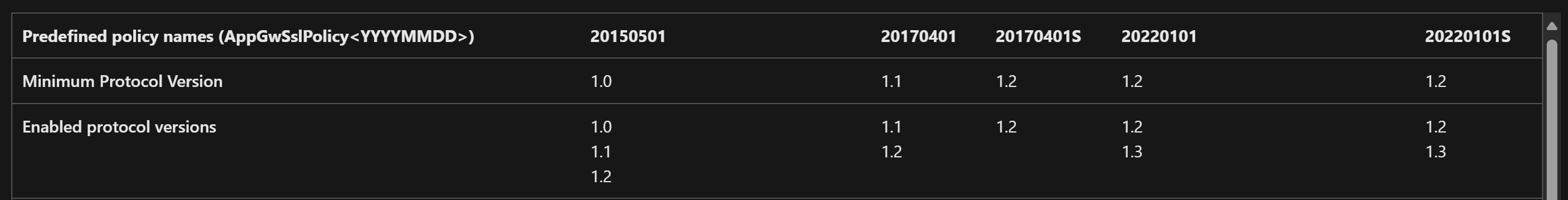
2. Verify Application Gateway SSL Policy
- In your Application Gateway, go to
Settings→Listeners - Note the
Selected SSL Policy - Check the policy’s supported TLS versions in the Microsoft documentation. Predefined policies like
AppGwSslPolicy20220101are recommended for security and compatibility.
3. Align TLS Versions
The gateway must allow the minimum TLS version enforced by the backend. For exaample:
- If backend enforces TLS 1.3
- The Application Gateway must permit TLS 1.3 or higher
Apart from that, ensure ciphers allowed by the gateway include at least one cipher suite the backend accepts.
4. Update SSL Policy
Choose a predefined policy that matches your security requirements. Microsoft’s recommended policy (AppGwSslPolicy20220101 at the time of writing) usually provides the best balance of security and compatibility.
We first see how to update the policy by using CLI commands:
az network application-gateway update \
--name <application-gateway-name> \
--resource-group <rresource-group-name> \
--set sslPolicy.policyType=Predefined sslPolicy.policyName=AppGwSslPolicy20220101
And this is the Infrastructure as Code Solution by using Bicep:
resource applicationGateway 'Microsoft.Network/applicationGateways@2021-05-01' = {
// ... other properties
properties: {
// ... other properties
sslPolicy: {
policyType: 'Predefined'
policyName: 'AppGwSslPolicy20220101' // Current recommended policy
}
}
}
Best Practices
- Always use the latest recommended SSL policy unless you have specific compatibility requirements
- Document any custom TLS version requirements in your infrastructure code
- Regularly review and update your TLS configurations to maintain security
- Consider using Azure Policy to enforce minimum TLS versions across your resources