Create a new API Connection and Access Policy for connecting Your Azure Logic App to Blob Storage in Bicep
When building workflows with Azure Logic Apps (Standard), a common requirement is to connect securely to Azure resources such as Blob Storage. In this article, we’ll show how to automate the creation of API Connections and Access Policies using Bicep, enabling your Logic Apps to access Blob Storage securely. We’ll cover both authentication methods: Shared Key and Managed Identity.
Creating an API Connection with a Shared Key
A shared key is a traditional way to authenticate to an Azure Storage Account. You retrieve the storage account key and use it in your connection definition in your Bicep file:
var location = resourceGroup().location
var storageAccountName = 'yourStorageAccountName'
resource storageAccount 'Microsoft.Storage/storageAccounts@2022-09-01' existing = {
name: storageAccountName
}
resource blobStorageConnectionWithSharedKey 'Microsoft.Web/connections@2018-07-01-preview' = {
name: 'name-of-your-connection'
kind: 'V2'
location: location
properties: {
displayName: 'name-of-your-connection'
api: {
id: '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Web/locations/${location}/managedApis/azureblob'
}
parameterValues: {
storageaccount: storageAccountName
sharedkey: listKeys(storageAccount.id, storageAccount.apiVersion).keys[0].value
}
}
}
Key points:
- The API Connection resource is created in the current resource group
- The
nameanddisplayNameproperties can be customized - The
2018-07-01-previewversion ofMicrosoft.Web/connectionsis valid and can be used - The
api.idproperty must use/managedApis/azureblobfor Blob Storage
Once the API Connection is created, you can use it in your Logic App workflows. For example, add a Get blob content (V2) action to your workflow.
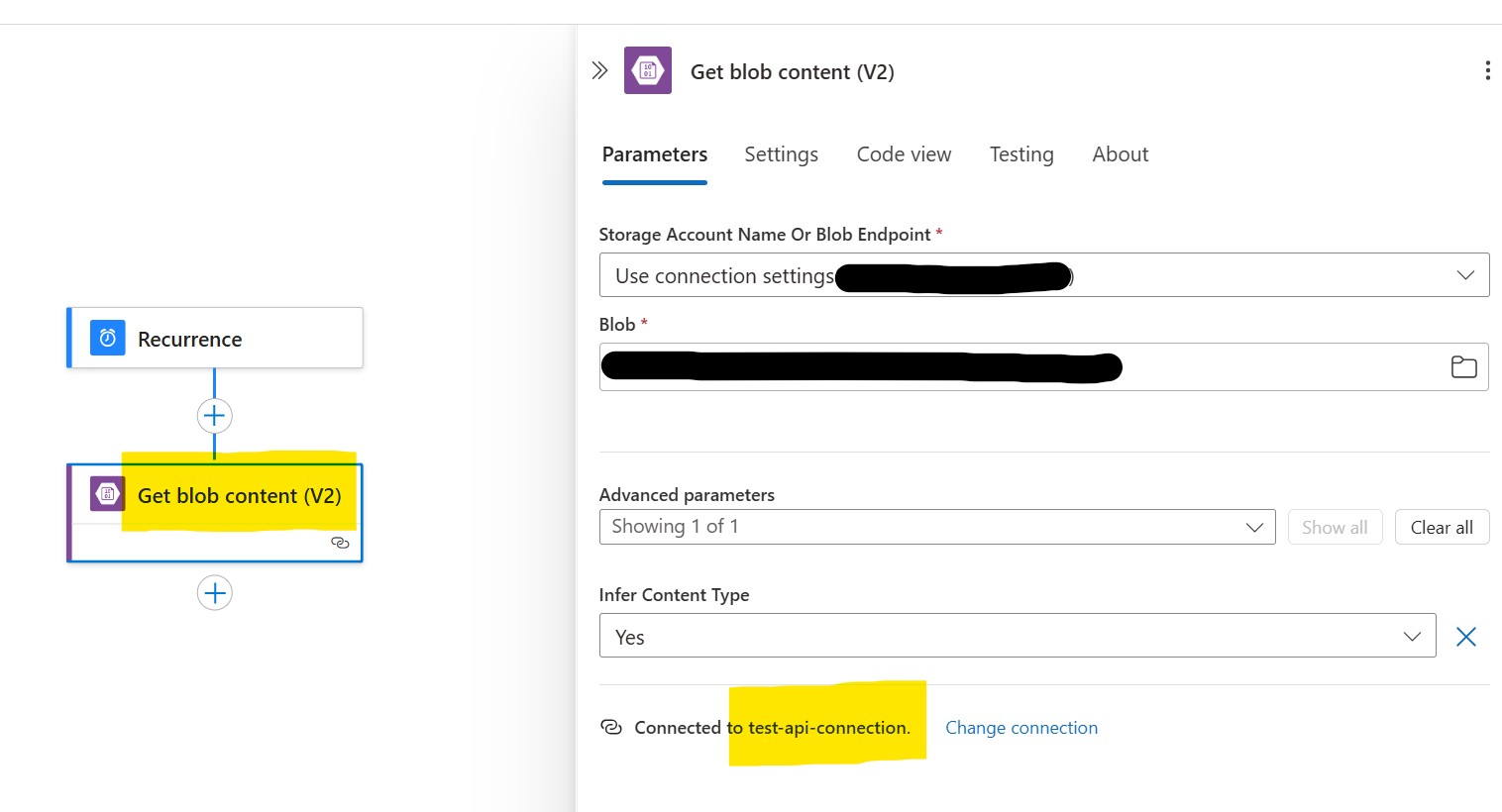
Note: The V2 actions in Logic Apps use API Connections, while older actions use Service Provider Connections.
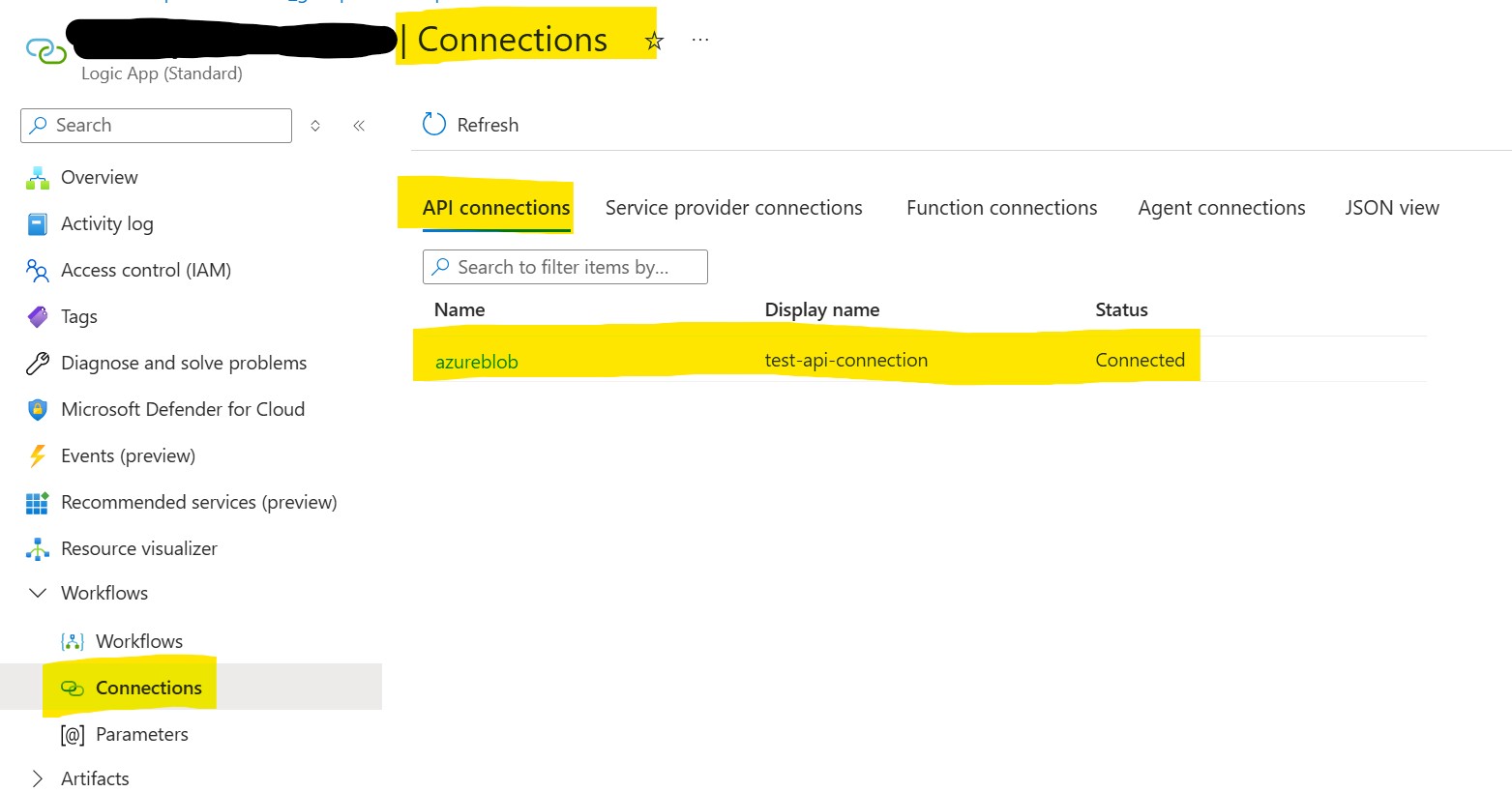
Creating an API Connection with a Managed Identity
Managed Identities provide a more secure and modern way to authenticate. Assign a User or System Managed Identity to your Logic App, grant it access to the Storage Account, and create an Access Policy for the API Connection.
Assuming you have already created a User Assigned Managed Identity, here’s how to automate the setup:
resource userManagedIdentity 'Microsoft.ManagedIdentity/userAssignedIdentities@2023-01-31' existing = {
name: 'name-of-your-managed-identity'
}
resource blobStorageConnectionWithManagedIdentity 'Microsoft.Web/connections@2018-07-01-preview' = {
name: 'name-of-your-connection'
location: location
kind: 'V2'
properties: {
displayName: 'name-of-your-connection'
api: {
id: '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Web/locations/${location}/managedApis/azureblob'
}
parameterValueSet: {
name: 'managedIdentityAuth'
values: {}
}
}
}
resource blobConnectionAccessPolicy 'Microsoft.Web/connections/accessPolicies@2018-07-01-preview' = {
parent: blobStorageConnectionWithManagedIdentity
name: 'name-of-your-access-policy'
location: location
properties: {
principal: {
type: 'ActiveDirectory'
identity: {
objectId: userManagedIdentity.properties.principalId
tenantId: subscription().tenantId
}
}
}
}
Key points:
- The Managed Identity must have the necessary permissions (e.g.,
Storage Blob Data Reader) on the Storage Account - The Access Policy resource links the Managed Identity to the API Connection
As with the Shared Key method, V2 actions in Logic Apps use API Connections, while older actions use Service Provider Connections.