The "No user assigned or delegated managed identity found for specified clientid/resourceid/principalid" in Azure and how to solve it
When working with Managed Identities in Azure you might encounter the error No user assigned or delegated managed identity found for specified clientid/resourceid/principalid.
But first of all let us see what a Managed Identity is and does.
What is a Managed Identity?
Managed Identities in Azure are a feature that allows Azure services to authenticate to other Azure resources without needing to manage credentials explicitly. They come in two types:
- System-assigned Managed Identity: Tied to a specific Azure resource and automatically managed by Azure.
- User-assigned Managed Identity: Created as a standalone resource and can be assigned to multiple Azure resources.
You can learn more about Managed Identities in the official Microsoft documentation.
When does this error typically occur
- The Managed Identity is not assigned to the Azure resource: For example, if you’re using an Azure Function to access Dataverse, the Managed Identity must first be explicitly assigned to the Function.
- The resource lacks the necessary permissions: Even if the Managed Identity is assigned to a resource, it must have the appropriate role or permissions to access the target resource.
- Incorrect client ID or principal ID: If you’re referencing the Managed Identity in your code or configuration, ensure the correct identifiers are used.
How to Resolve the Error
1. Verify the Managed Identity Assignment
Ensure the Managed Identity is assigned to the Azure resource you’re working with. For example, if you’re using an Azure Function:
- Navigate to the Azure Function in the Azure Portal.
- Go to the Identity section.
- Enable the System-assigned Managed Identity or assign a User-assigned Managed Identity.
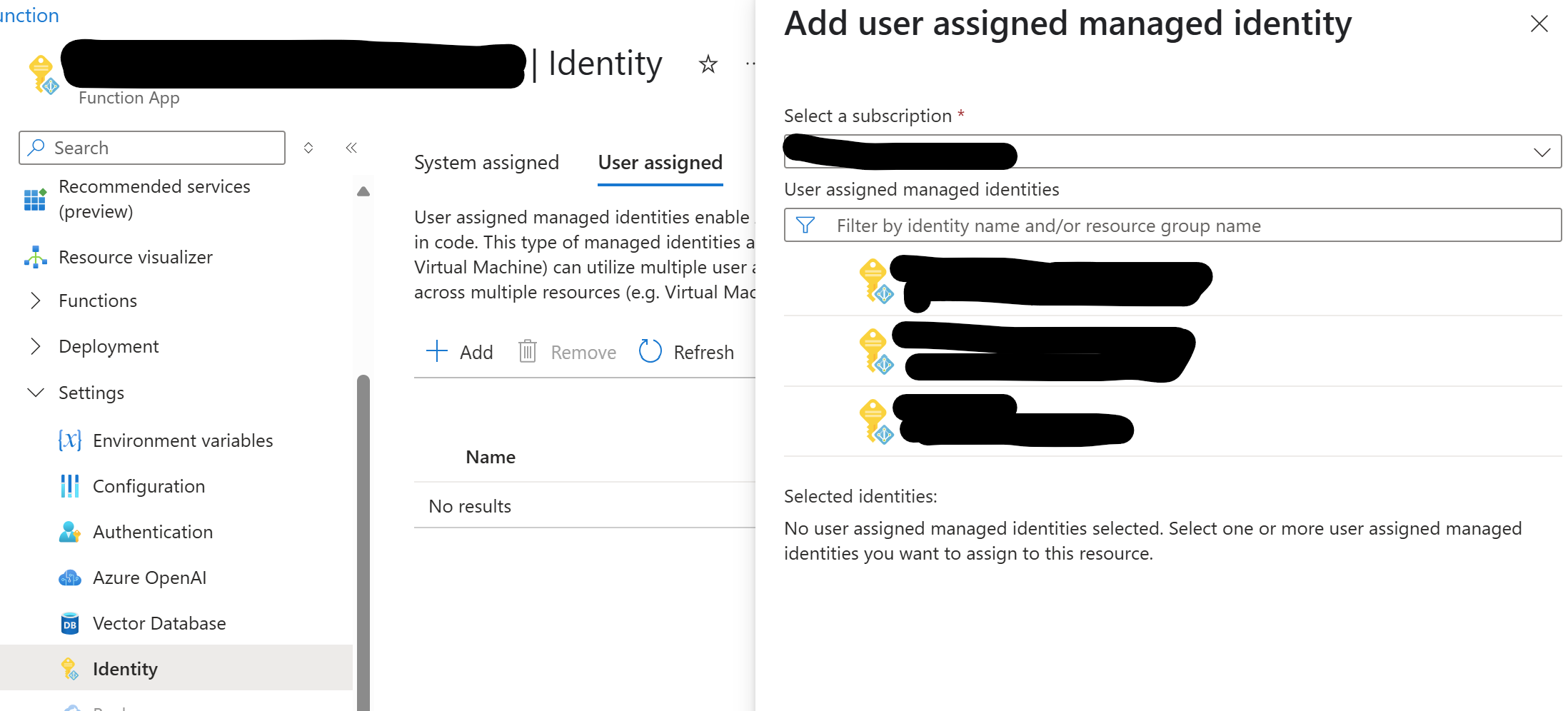
2. Check Role Assignments
The Managed Identity must have the necessary permissions to access the target resource. For example:
- If accessing Azure Key Vault, assign the Key Vault Reader or Key Vault Secrets User role.
- If accessing Dataverse, create a new
Application Userfor the Managed Identity in Dataverse with the needed roles.
3. Validate Configuration in Code
If you’re referencing the Managed Identity in your code and use the MSAL authentication, with the DefaultAzureCredential class, ensure the correct client ID or principal ID is used. In the following example you see how to access a Key Vault in Azure.
var credential = new DefaultAzureCredential(new DefaultAzureCredentialOptions
{
ManagedIdentityClientId = managedIdentityClientId
});
var client = new SecretClient(new Uri("https://<your-keyvault-name>.vault.azure.net/"), credential);
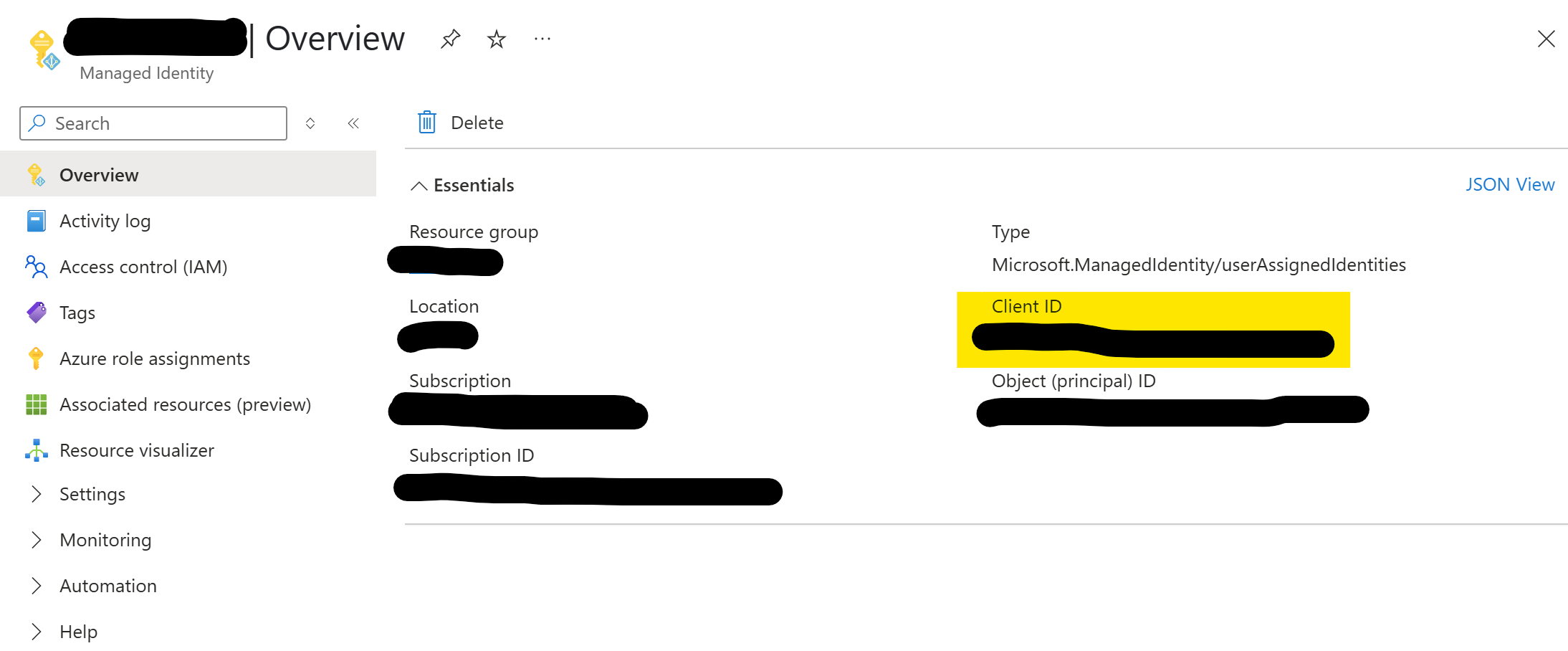
You can find the ClientId of the Managed Identity in the Azure Portal by searching for the Managed Identity with its name and then copying it:
Conclusion
The “No user assigned or delegated managed identity found” error is a common issue when working with Managed Identities in Azure. By ensuring the Managed Identity is properly assigned, has the correct permissions, and is correctly referenced in your code, you can resolve this error and securely access Azure resources.